
Cybermidnight Club– Hackers, Cyber Security and Cyber Crime
Cybermidnight Club– Hackers, Cyber Security and Cyber Crime is a trailblazing podcast by Alberto Daniel Hill, an expert in cybersecurity and the first person in Uruguay to serve prison for a computer-related crime. A crime he isn’t guilty of, perhaps one which never happened. Join Alberto as he dives deep into the world of hackers and cybersecurity in his riveting podcast. In this series, Alberto provides firsthand insights into the dark web and expert analysis of cybersecurity issues that are central to our present digital age.
Episodes

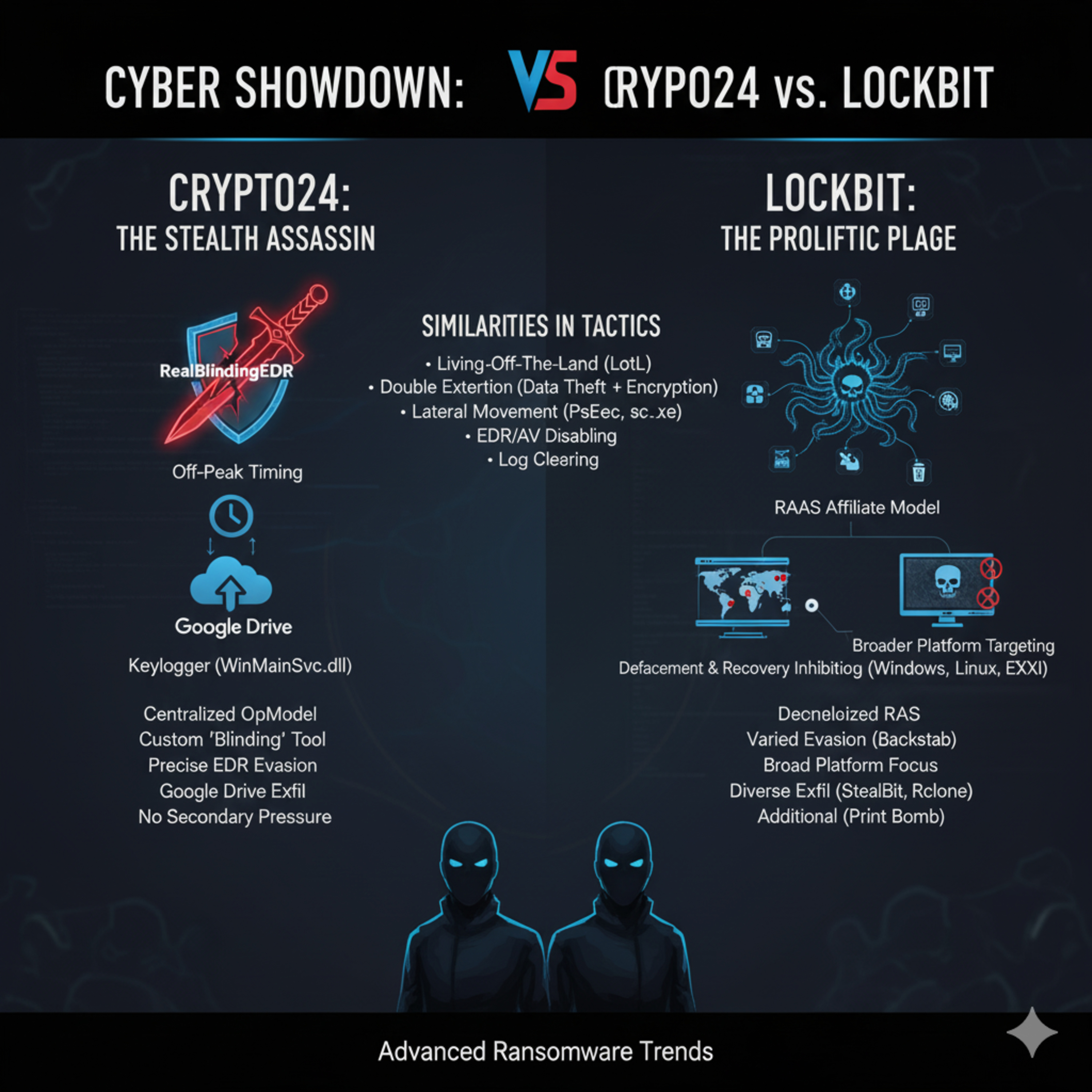
Crypto24 Ransomware: Stealth Attacks Blending Legitimate Tools
These sources provide a detailed comparative analysis of two significant ransomware threats: Crypto24 and LockBit. The first source offers a side-by-side comparison, establishing that LockBit operates as a massive Ransomware-as-a-Service (R…
Crypto24 Ransomware: Stealth Attacks Blending Legitimate Tools
These sources provide a detailed comparative analysis of two significant ransomware threats: Crypto24 and LockBit. The first source offers a side-by-side comparison, establishing that LockBit operates as a massive Ransomware-as-a-Service (R…

The Crypto24 Playbook: An Analysis of the Banco Hipotecario del Uruguay Ransomware Campaign
The sources consist of an in-depth LinkedIn article detailing the Crypto24 ransomware attack on a bank and a LinkedIn error page that suggests alternative content to explore. The article, written by Michael Slowik, explains how the Crypto24…

Uruguay’s Digital Sovereignty Battle Combating Corporate Censorship with Labor Law and Algorithmic Transparency
A Regulatory Crossroads for Uruguay’s Digital FutureUruguay stands at a critical juncture in the formation of its digital policy, navigating a landscape defined by a stark “policy bifurcation.” This division is evident in the contrast betwe…

John McAfee's Final Interview: On the Run, Crypto, and Psychedelics.
The source provides excerpts from a transcript of a video interview with John McAfee, the British-American computer programmer and founder of the McAfee software company. McAfee, who notes he and his wife Janice are on the run from US autho…

Briefing de Políticas: La Intersección de Vulnerabilidades Cibernéticas, Corrupción Sistémica y Poder del Crimen Organizado en México
Un Nuevo Paradigma de Amenaza HíbridaEste briefing tiene como propósito analizar la convergencia de tres fuerzas que están redefiniendo el panorama de la seguridad en México: la creciente sofisticación tecnológica del crimen organizado, la…

El Secuestro Digital del Banco Hipotecario: Crónica de un Ciberataque Anunciado
Cuando se Apagaron las LucesEl 30 de septiembre de 2025, una sombra digital se cernió sobre Uruguay. El Banco Hipotecario (BHU), una entidad estatal clave para la vivienda y la economía del país, sufrió un apagón total en su red. Este event…

The Sky is Leaking: A Case Study on Unencrypted Satellite Data
The source, a transcript from a YouTube video titled "HACKEAN A LA GUARDIA NACIONAL," discusses a critical cybersecurity vulnerability involving geo-stationary satellites where sensitive data is transmitted unencrypted. Researchers from the…

El Cielo Espía: Cómo una Antena Satelital Reveló Secretos a Plena Vista
En la azotea de una universidad, un grupo de “cerebritos”, como los llama su fuente, apuntó una antena hacia el cielo. No buscaban estrellas ni señales extraterrestres. Buscaban secretos. Y con un equipo de apenas 14,000 pesos mexicanos, en…

Huawei: La Historia del Gigante Tecnológico y la Operación Secreta que lo Acechó
1. Introducción: Un Router Comprometido en IránEn 2010, un router Huawei recién instalado en la oficina de un político iraní se convirtió en la herramienta de vigilancia perfecta. Sin que nadie lo supiera, una falla de diseño permitía a un …

The Dragon's Network: Huawei, the NSA, and the Secret War for Global Tech Supremacy
The source provides an overview of Operation Shotgiant, a sophisticated cyber-espionage effort by the National Security Agency (NSA) of the United States targeting the Chinese telecommunications giant, Huawei. The operation began with an ef…

La Historia de Shady Rat: El Ciberataque que Redefinió el Espionaje Digital
Introducción: Un Cebo en la RedEn diciembre de 2012, el investigador de ciberseguridad Kyle Wilhoit lanzó un experimento fascinante. Creó una planta de tratamiento de agua completamente virtual, con sistemas de control industrial, documenta…

Operation Shady Rat: China's Cyber Espionage Engine
The source provides an overview of Operation Shady Rat, a long-running, extensive campaign of cyber-espionage attributed to a unit of the Chinese military (Unit 61398) starting around 2006. This operation involved Advanced Persistent Threat…

De lo Falsificado a lo Digital: La Sorprendente Evolución del Imperio Criminal de Corea del Norte
Introducción: El Asalto de los $600 MillonesEn marzo de 2022, millones de jugadores del popular videojuego Axie Infinity comenzaron a experimentar algo extraño. Lo que al principio parecía una simple falla técnica —algunas funciones dejaron…

From Super Dollars to Super Hackers: The Secret History of North Korea's Criminal Empire
The video transcript explores the phenomenon of highly effective North Korean state-sponsored hacking, contrasting this technological prowess with the nation's overall economic poverty and technological isolation enforced by its Juche ideol…

La Guerra por la PS3: La Historia del Hackeo a PlayStation Network
Introducción: El Apagón que Conmocionó al Mundo de los VideojuegosEl 20 de abril de 2011, el universo de los videojuegos se detuvo. Sin previo aviso, una fuerza misteriosa desconectó la PlayStation Network (PSN) de Sony, sumiendo a millones…

The Sony PlayStation Network Hack
The source, an excerpt from a YouTube video transcript, offers a detailed account of the events surrounding the 2011 PlayStation Network (PSN) hack. It begins by introducing George "GeoHot" Hotz, a renowned hacker who first gained fame by j…

Saving Samantha
The sources comprise a transcript of a YouTube video titled "Saving Samantha on Twitter Spaces" and a Spotify podcast listing for the same event, hosted by the "Cybermidnight Club – Hackers, Cyber Security and Cyber Crime." The primary sour…

Hacking hears and minds.
The provided texts offer two distinct perspectives on modern forms of influence and security, with the Darknet Diaries podcast excerpts exploring the history and function of PSYOP (Psychological Operations), or Military Information Support …

The Soul of the Machine: A Beginner’s Guide to “The Hacker’s Manifesto”
1. Introduction: The Voice from the WiresIt’s 1986. The headlines are stark and sensational: “Teenager arrested in computer crime scandal”, “Hacker arrested after bank tampering”. To the public, these are simple stories of digital delinquen…
The Unsafe Space: A Story of a Conversation Gone Wrong. Social media, social audio, twitter, x
Introduction: The Promise of a Safe Place OnlineOn the internet, a “safe space” is a powerful idea. It’s meant to be a community where people can share difficult, painful experiences—especially when they feel wronged by powerful systems lik…
The Uruguayan Cyber-Dilemma: A Deep Dive into National Strategy, Legal Enforcement, and the Transparency Deficit (2024–2025)
The Uruguayan Cyber-Dilemma—A Critical AnalysisPresenter: Alberto Daniel Hill (Ethical Hacker, Forensic Expert, and Defender of Knowledge)Part 1 of 4: The Personal Cost of Transparency and the True Ethos of HackingI stand before you today n…
Analysis of Twitter Space: “Ecos del Pasado en la Era Digital”
The source text is comprised of excerpts from a long-form, multi-topic audio discussion, which covers a wide array of subjects including personal relationships and intimacy, as indicated by early commentary on communication and sexual expre…
The takedown of the ‘Dictadores’ syndicate was not the story of a lone hacker in a basement. It was the dismantling of a structured, professional criminal organization
The takedown of the ‘Dictadores’ syndicate was not the story of a lone hacker in a basement. It was the dismantling of a structured, professional criminal organizationIntroduction: Two Hackers, Two Different WorldsIn Argentina, law enforcem…

Análisis de la Regulación de Plataformas Digitales en Uruguay
Análisis de la Regulación de Plataformas Digitales en UruguayResumen EjecutivoEl panorama regulatorio de las grandes plataformas digitales en Uruguay se caracteriza por una marcada bifurcación de políticas, avanzando en dos vías paralelas y…

Análisis de la Regulación de Plataformas Digitales en Uruguay
La regulación de las plataformas digitales en Uruguay se desarrolla a través de dos trayectorias legislativas distintas y paralelas.Este camino legislativo, impulsado por el Poder Ejecutivo, se centra en establecer protecciones mínimas para…

Uruguay's Dual Digital Platform Regulation: Labor and Democratic Governance
The source provides an extensive analysis of Uruguay's efforts to regulate large digital platforms, identifying two distinct legislative tracks that characterize the nation's digital governance landscape. The first track successfully establ…

Hactivism, Detention, and Digital Justice: Unpacking a Latin American Cybercrime Saga
These sources consist of transcripts from YouTube videos by the channel “CYBERMIDNIGHT CLUB,” primarily focusing on interviews and statements from a hacker known as Gob or Gob Etherium. The central topic is the arrest and imprisonment of Go…

Red Flag Forensics: How to Spot Stalkers, Scammers, and Cannibals on Dating Apps
A Beginner's Guide to Spotting Red Flags in Online DatingIntroduction: Trusting Your Gut in the Digital Dating WorldOnline dating offers exciting possibilities, but your safety must be your first priority. This guide is not meant to scare y…

The Parmaster: Underground: Hacking, Madness, and Obsession on the Electronic Frontier
The provided excerpts, primarily sourced from Suelette Dreyfus and Julian Assange's work "Underground," examine the early culture, motives, and legal challenges faced by the international computer underground, particularly focusing on Austr…

Putin’s Bears: World’s Most Dangerous Hackers
Case Study: Russian State-Sponsored Cyber Operations and their Geopolitical ImpactIntroduction: The Threat Doctrine of the "Bears"Russian state-sponsored cyber units, colloquially known as the "Bears," operate as direct instruments of natio…

Argentina: Una Historia de Hackers
De la Crisis al Ciberdelito: La Historia del Hacking en Argentina1. Introducción: El Nacimiento de una Cultura ÚnicaLa cultura hacker en Argentina no surgió en un laboratorio tecnológico ni en un próspero entorno corporativo. Fue forjada en…

Estudio de Caso: Anatomía de una Estafa Cripto con Deepfakes de Elon Musk
Estudio de Caso: Anatomía de una Estafa Cripto con Deepfakes de Elon Musk1.0 Introducción: El Advenimiento de las Estafas Potenciadas por IALas estafas en línea han evolucionado significativamente desde sus primeras iteraciones. Tácticas qu…

La Trampa de Tinder
La Trampa de TinderThe sources present a composite study of the dangers of online dating and the emergence of an unconventional media platform dedicated to cybersecurity and digital advocacy. One set of transcripts details several chilling …

La Crisis Digital de Uruguay
Un Análisis Exhaustivo de la Catástrofe Cibernética del Gobierno Uruguayo: Fallos Sistémicos, el Compromiso Fatal de 30.000 Certificados PKI de Identidad Nacional, y la Peligrosa Brecha entre la Ambición Digital y la Ineptitud Operacional.F…

Uruguay's Digital Breach: A Crisis of Trust and Security
Analysis of Systemic Cybersecurity Failures in the Uruguayan GovernmentExecutive SummaryThis briefing analyzes a series of large-scale data breaches targeting Uruguayan government entities, which starkly contradict the nation's reputation a…

Anonymous: We Are Legion. Expect Us.
Anonymous: We Are Legion. Expect Us.Dive into the chaotic world of Anonymous, the decentralized computer hacker group and serious political movement that became known as the "final boss of the internet". Anonymous is a collective of nameles…

The Strategic Paradox: Inside Peru's Escalating Cyber Crisis—From Hacktivism to RaaS Extortion
Title: The Strategic Paradox: Inside Peru's Escalating Cyber Crisis—From Hacktivism to RaaS ExtortionDescription:In this episode, we dive deep into the dramatic escalation of cyber threats gripping Peru, a nation where rapid digital integra…

The Prophet and the Storm
The Prophet and the StormCybersecurity expert Alberto Daniel Hill delivers an unflinching analysis of the moment Uruguay’s celebrated reputation as a digital pioneer collapsed, arguing that the catastrophic 2025 BHU ransomware attack was no…
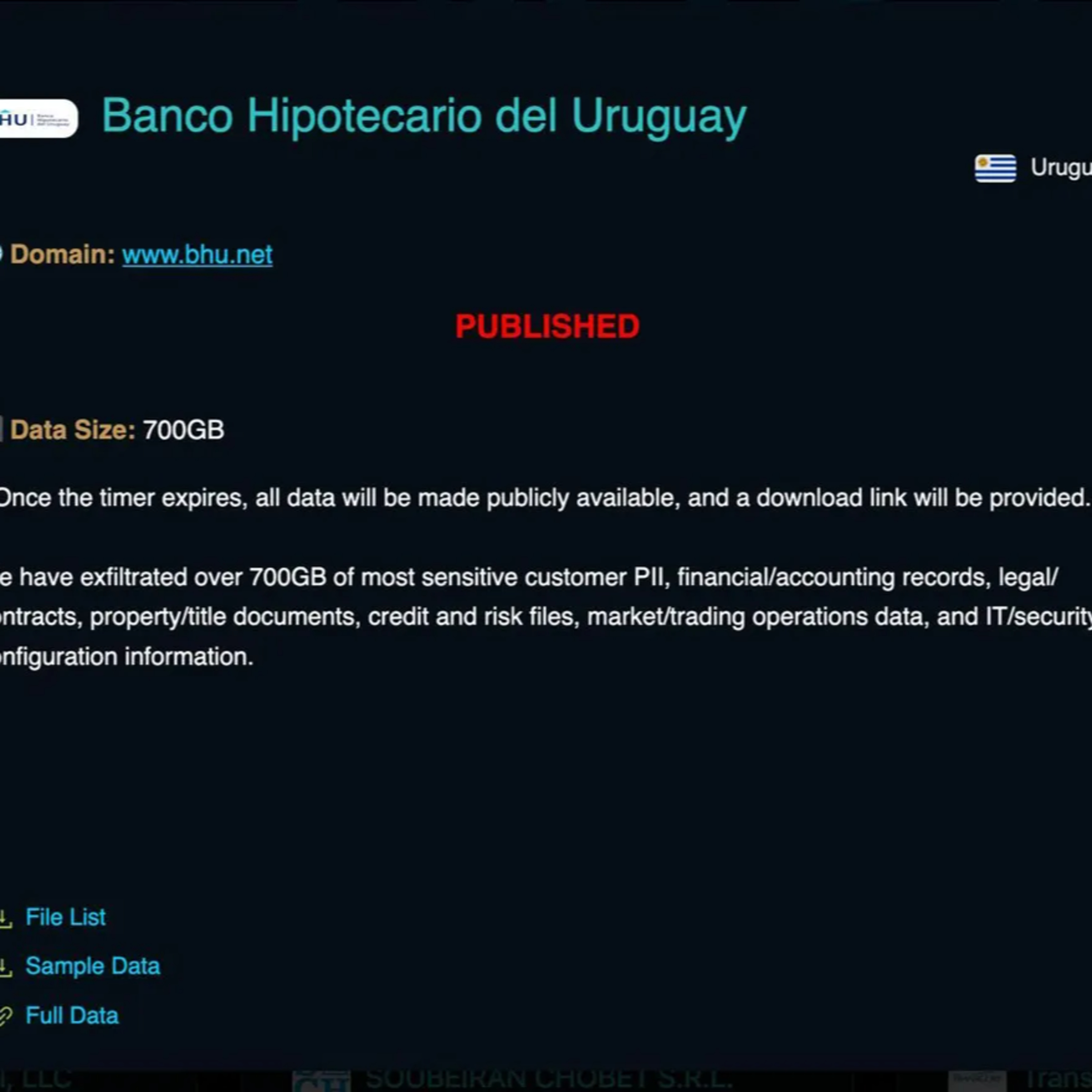
The BHU Data Breach
The BHU Data Breach: How Uruguay’s Digital Star Fell Victim to the Crypto24 Ransomware and 95% Weak PasswordsIn September 2025, the state-owned Banco Hipotecario del Uruguay (BHU) suffered a catastrophic systems failure. While the instituti…